Disclaimer: Technical controls should be utilized wherever and whenever possible. Please don't take automation as the bible for passing audits you must ensure that controls that are in-line with your industry and your organization in most cases controls are related to regulations.
Cloud Security Compliance in a lot of enterprises has not been planned and thought out ahead of time. Basically, organizations wait until some audit comes around and then everyone rushes to ensure they are compliant, just to pass either their internal audit or external audit.
Humans start running around in a circle to remediate issues that they deemed related to “compliance” or “security”, hiring vendors and contractors to perform in this elaborate production to ensure that they pass their audit, but in reality, it’s just another play going on at The Risk Management Theatre.
In Agile compliance-focused enterprises and business, compliance and security solutions are incrementally built, and in most cases codified. Now the Security team members are no longer just actors performing, but they are truly implementing value-added actions, thus the illusion of security and/or compliance is not just a bunch of written documentation that can’t be measured or validated.
The traditional way of implementing security compliance the waterfall model, whereas full patterns and controls must be defined and committed in detail. This is not the agile model nor can it scale in this fast paced ever-changing public cloud environment.
I do understand that not all companies are ready to move to a strictly automated event-driven security model, nor do I recommend it. However, I do recommend at least a partially automated workflow to optimize security team capabilities.
This article is the first of a two-part editorial for those companies that still follow a quasi-waterfall model and want to enhance their compliance posture by using an automated workflow solution.
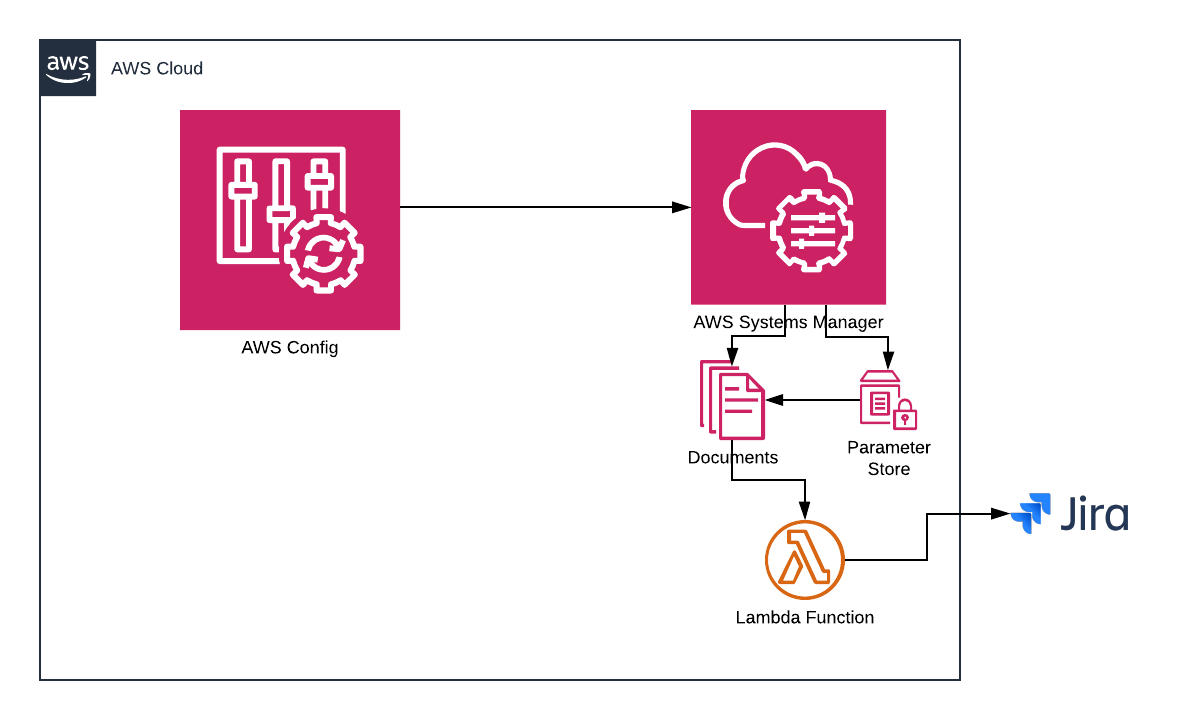
In this article, I will describe a few components to integrate your Cloud Continuous Security model. The bulk of these services are native to the AWS environment and are often overlooked for vendor tools. In most cases, these vendor tools integrate with AWS native Security solutions.
For this solution, I will be using AWS Config, Config Rules, AWS System Manager, SSM Automated Document, and Jira.
Below is a description of each service in more detail:
AWS Config — AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations [source]
AWS Custom Config Rules -AWS Config provides AWS managed rules, which are predefined, customizable rules that AWS Config uses to evaluate whether your AWS resources comply with common best practices. For example, you could use a managed rule to quickly start assessing whether your Amazon Elastic Block Store (Amazon EBS) volumes are encrypted or whether specific tags are applied to your resources. You can set up and activate these rules without writing the code to create an AWS Lambda function, which is required if you want to create custom rules. The AWS Config console guides you through the process of configuring and activating a managed rule. You can also use the AWS Command Line Interface or AWS Config API to pass the JSON code that defines your configuration of a managed rule. [source]
AWS System Manager- AWS Systems Manager gives you visibility and control of your infrastructure on AWS. Systems Manager provides a unified user interface so you can view operational data from multiple AWS services and allows you to automate operational tasks across your AWS resources. With Systems Manager, you can group resources, like Amazon EC2 instances, Amazon S3 buckets, or Amazon RDS instances, by application, view operational data for monitoring and troubleshooting, and take action on your groups of resources. Systems Manager simplifies resource and application management, shortens the time to detect and resolve operational problems, and makes it easy to operate and manage your infrastructure securely at scale. [source]
AWS System Manager Automation Document -Systems Manager Automation document defines the Automation workflow (the actions that the Systems Manager performs on your managed instances and AWS resources). Automation includes several pre-defined Automation documents that you can use to perform common tasks like restarting one or more Amazon EC2 instances or creating an Amazon Machine Image (AMI). Documents use JavaScript Object Notation (JSON) or YAML, and they include steps and parameters that you specify. Steps run in sequential order. [source]